Oficialu: „Intel“ procesoriai turi saugumo spragų, gali būti paveikti ir kiti gamintojai
„Google“ mokslininkai suradę modernių procesorių saugumo spragas jas pavadino „Meltdown“ (liet. sulydimas) ir „Spectre“ (liet. šmėkla). Tam netgi sukurti specialūs tinklapiai. Panašu, kad šių saugumo klaidų yra labiausiai paveikti „Intel“ procesoriai. Tuo tarpu AMD produkcija, dėl visiškai kitokios architektūros, tikimasi, kad turi nulinį pažeidžiamumą, ar arti to. Kaip praneša patys ARM, jų architektūra irgi neturi surastų saugumo spragų.
„Intel“, nenorėdami atrodyti visai blogai, savo pranešime įtraukė ARM ir AMD pavadinimus, nors konkurentų procesoriai „Google“ surastų saugumo spragų neturi, ar jų kol kas nebuvo rasta. Taip norima sušvelninti susidrausią situaciją, kad blogai neatrodytų vien tik mėlynasis milžinas. Manoma, kad šių saugumo klaidų neįmanoma pataisyti neprarandant spartos. Tai dar, žinoma, priklauso nuo atliekamo darbo su procesoriais.
Visų didžiųjų kompanijų oficialūs pranešimai:
The Project Zero researcher, Jann Horn, demonstrated that malicious actors could take advantage of speculative execution to read system memory that should have been inaccessible. For example, an unauthorized party may read sensitive information in the system’s memory such as passwords, encryption keys, or sensitive information open in applications. Testing also showed that an attack running on one virtual machine was able to access the physical memory of the host machine, and through that, gain read-access to the memory of a different virtual machine on the same host.
These vulnerabilities affect many CPUs, including those from AMD, ARM, and Intel, as well as the devices and operating systems running them.
As soon as we learned of this new class of attack, our security and product development teams mobilized to defend Google’s systems and our users’ data. We have updated our systems and affected products to protect against this new type of attack. We also collaborated with hardware and software manufacturers across the industry to help protect their users and the broader web. These efforts have included collaborative analysis and the development of novel mitigations.
We are posting before an originally coordinated disclosure date of January 9, 2018 because of existing public reports and growing speculation in the press and security research community about the issue, which raises the risk of exploitation. The full Project Zero report is forthcoming.
Source: Google, Project Zero
AMD
There is a lot of speculation today regarding a potential security issue related to modern microprocessors and speculative execution. As we typically do when a potential security issue is identified, AMD has been working across our ecosystem to evaluate and respond to the speculative execution attack identified by a security research team to ensure our users are protected.
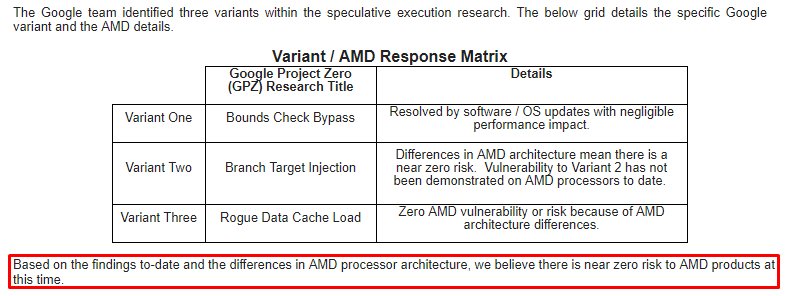
To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD’s architecture, we believe there is a near zero risk to AMD processors at this time. We expect the security research to be published later today and will provide further updates at that time.
ARM
This method requires malware running locally and could result in data being accessed from privileged memory. Our Cortex-M processors, which are pervasive in low-power, connected IoT devices, are not impacted.
Intel
Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data.
Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.Intel is committed to product and customer security and is working closely with many other technology companies, including AMD, ARM Holdings and several operating system vendors, to develop an industry-wide approach to resolve this issue promptly and constructively. Intel has begun providing software and firmware updates to mitigate these exploits. Contrary to some reports, any performance impacts are workload-dependent, and, for the average computer user, should not be significant and will be mitigated over time.
Intel is committed to the industry best practice of responsible disclosure of potential security issues, which is why Intel and other vendors had planned to disclose this issue next week when more software and firmware updates will be available. However, Intel is making this statement today because of the current inaccurate media reports.
Check with your operating system vendor or system manufacturer and apply any available updates as soon as they are available. Following good security practices that protect against malware in general will also help protect against possible exploitation until updates can be applied.Intel believes its products are the most secure in the world and that, with the support of its partners, the current solutions to this issue provide the best possible security for its customers.
Microsoft
We’re aware of this industry-wide issue and have been working closely with chip manufacturers to develop and test mitigations to protect our customers. We are in the process of deploying mitigations to cloud services and have also released security updates to protect Windows customers against vulnerabilities affecting supported hardware chips from Intel, ARM, and AMD. We have not received any information to indicate that these vulnerabilities had been used to attack our customers.













Kiek teko girdėti spartos kritimas priklausys nuo procesoriaus ir sieks nuo 5 iki 30 proc… Tai jei 8700K sparta kris iki 30 proc… tai į ką šis procas bus panašus? 🙂
Į buldozerį? 😀

Bijau, kad kazkas panasaus dabar pas juos gali is tikro but: 😀 https://youtu.be/O90zrOS18t4?t=43
Ziniasklaida be gailestio trypia Intel’i, kad net biski gaila jodarosi jau net 🙂 Aisku pats durnas, kad savo pranesime bande issivartyt, o ne aiskiai prisieme atsakomybe.
Tai su išisvartymu prieš metus ar du būtų be problemų, nes alternatyvų nebuvo. Dabar prasčiau kai Ryzen geri procesoriai yra pasirinkime.
Geras video 😀
AMD galėtų visiškai ramiai paduoti Intel už melagingai paskleistą informaciją, jeigu paaiškėtų kad AMD procesorių saugumo spraga tikrai neliečia. Būtų dar vienas smūgis.
Techniskai Intel’is nemelavo, tik kaip lape sukdamas uodega vartesi 🙂 Tiek Intel, tiek AMD su ARM (siaip viskas, kas naudoja speculative execution) yra pazeidziami „spectre“ tipui, o fix’ai bus programineje irangoje ir netures jokiu nasumo sumazejimu. Esme ta, kad Intelis prisidenge „spectre“ pazeidziamumu, kuris galioja visiems, tam, kad issivartytu is „meltdown“ bedos, kuri yra (siai dienai bent) Intel-only, ir kuriai reikia to workaround’o, kuris kerta per nasuma. Lievas PR ejimas is Intel ir tiek.
Šiaip liečia, yra 3 variantai pažeidžiamumo, trečias variantas yra „Meltdown“ kaip suprantu. 1 variantas pataisomas su OS ar softo patchu, 2 variantas yra beveik nulinis ir iki šiol nieks neparodė kad gali juo pasinaudot ant AMD procu. https://www.amd.com/en/corporate/speculative-execution
nu nezinau….chebra, na realiai truksta info kas kur kaip kada…
Kai buvo problema su Intel tuo ME…viskas buvo aisku. Na dabar antra naujiena, bet taip ir neaisku, kur ir pas ka ta skyle
https://www.youtube.com/watch?v=d7ILCoU9d4k
Neeeee, man manasis i7 6700K taip patiko. 🙁 Blogiausiu atveju pasikeisiu CPU + MB į Ryzen ir gerai. AMD bus didžiulis pliusas, thanks to Intel. 😀